North Korean hacker group Lazarus is responsible for at least five attacks on cryptocurrency exchanges, looting an estimated $571.3 million US according to a report by cyber security company Group-IB.
The annual Hi-Tech Crime Trends publication analyses data from 14 hacks in the past 18 months and builds security solutions to combat the latest hacker technology.
This year’s report found Lazarus responsible for the notorious Coincheck attack in which $534 million US was stolen. Group-IB also believes the North Koreans targeted Japanese crypto-currency exchange Zaif, in a case reported on by Bitcoin Australia.
Group-IB CTO Dmitry Volkov announced the results at the sixth international CyberCrimeCon conference in Moscow. In his speech, Mr. Volkov warned that the number of hacks will only increase.
“Last year we warned that hackers competent enough to carry out a targeted attack might have a new target – cryptocurrency exchanges. And at the beginning of 2018, hackers’ interest in cryptocurrency exchanges ramped up.”
Mission: Unknown
The motivations of Lazarus, asides from capital gain, are unknown. The group is sponsored by the North Korean government, and many speculate the hackers are trying to wreak global havoc.
According to Kaspersky, Lazarus is the same culprit behind the infamous Sony hack in 2014. Hackers accessed the entertainment company’s servers and leaked confidential information all over the internet.
In an operation code-named ‘Blockbuster’, Kaspersky joined with analytics companies Novetta and AlienVault to prove Lazarus was to blame.
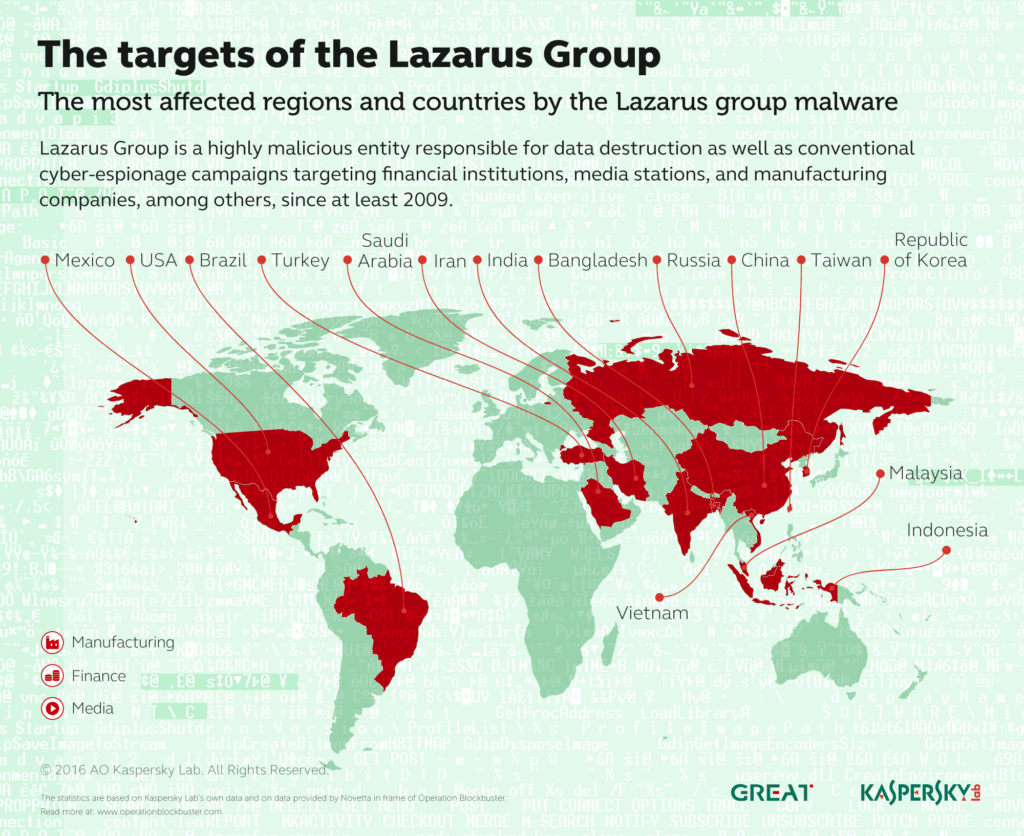
The investigation revealed Lazarus had dealings with military espionage and was behind a slew of efforts to sabotage financial institutions, businesses and media stations.
A Strong Offense is the Best Defense
The hackers have established a clear pattern during attacks on corporate networks, in a strategy called spear phishing.
Potential victims will receive malware sent to them under the guise of legitimate email traffic. This may include emails with subjects like “Engineering Manager for Cryptocurrency Job” or contain attachments like “Investment Proposal”, according to Group-IB.
After compromising the local network, Lazarus gets busy finding cryptocurrency wallets stored on workstations and servers. It only takes moments for the hackers to steal millions of dollars.
Initial Coin Offerings are especially good targets, and Group-IB predicts the number of threats is set to rise. The company reports that,
“Fraudulent phishing-schemes involving crypto-brands will only get more complex as well as cybercriminals’ level of preparation for phishing attacks. Automated phishing and the use of so-called ‘phishing-kits’ will become more widespread, including for the attacks on ICOs.”
But it isn’t all bad news. Once an anonymous enemy, Lazarus is now a known and identified entity. Last month, the US Department of Justice announced charges against one of its members who participated in the Sony hack.
And while Lazarus still poses a serious threat, cryptocurrency exchanges are quickly learning to build stronger defences. Users are better understanding the risks of leaving their wallets connected to the exchanges as well.
To learn more about how to keep your wallet safe, visit this page for more information.